Background
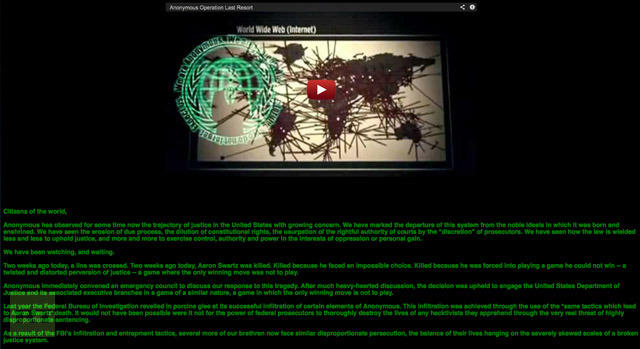
On January 25th, 2013, a faction within Anonymous launched the Twitter account @OpLastResort with links to several videos criticizing the U.S. Justice Department’s treatment of computer programmer and Internet activist Aaron Swartz prior to his suicide.
Notable Developments
USSC Website Takedown
On January 26th, 2013, the website of the United States Sentencing Commission (USSC)[45] was defaced with a video message lamenting “the erosion of due process, the dilution of constitutional rights, the usurpation of the rightful authority of courts by the ‘discretion’ of prosecutors." (shown below)
Operation Last Resort
Anonymous claimed responsibility for the cyberattack against the U.S. Justice Department in retaliation for the prosecution that the group say ultimately led him to commit suicide and announced the launch of Operation Last Resort, threatening to release “warhead” files that contain sensitive information on individuals in the Justice Department. Within 48 hours, the video received more than a million views, 5,000 up votes and 3,600 comments and the event was covered by Gawker[44] and The Verge[48] among others.
On January 27th, @OpLastResort[46] tweeted the well-known Konami cheat code with an instruction to input the code on the U.S.S.C website. According to Slate, typing in the code initiated a flash-based game with the alert message “”/memes/pew-pew">PEW PEWPEWPEWPEW! End Prosecutorial Overreach!" in which the visitor could control a missile-enabled Nyan Cat and shoot chunks of text off the government page. Later that day, the website of the U.S. Probation Department for the Eastern District of Michigan was taken down by another attack in a similar fashion, presumably carried out by the members of Anonymous.
ussc.gov
— OpLastResort (@OpLastResort) January 27, 2013-> enter Konami code (with cursor keys) ↑↑↓↓←→←→ B A <Enter> --> CAEK#opLastResort
Authenticity Questioned
On January 26th, a list of alleged encryption keys to the so called “warhead files” allegedly obtained from the USSC was released via Pastebin. The following day, The Daily Dot reported that it had received an anonymous e-mail purportedly containing hundreds of names and addresses attributed to the Witness Protection Program, but later speculated that the files could be a hoax, citing the claim of @AnonymousIRC that the file comprised of data “ripped from a two year old document.” On January 27th, a possible decryption of the warhead files was posted to The Pirate Bay by a user known as “zingelll.” According to zingelll, the translated keys contained several messages addressed to the decoder, including:
* “G00DLUCKPH4GG0T”
- “YOUWONTBEABLETOCRACKTHIS
- “BECAUSEYOUREADUMBBITCH”
- “HAVEFUNTHOUGHBECAUSEITWASFUNFORME”
On January 29th, The Daily Dot followed up on the hoax rumor with corroborated claims from members of an Anonymous faction known as Anonymous X-SecT. Among them was Joe Falzano, who launched a Change.org petition urging those spreading the files to cease and desist. The following day, Falzano posted a Pastebin message expressing his skepticism towards the authenticity of Operation Last Resort:
“ALL credible sources/anon cells to date have no idea who is running this operation. It came out of thin air and is using old anon operations data claiming its new.”
Search Interest
External References
[1]Gawker – Anonymous Hacks Department of Justice Website
[2]USSC– United States Sentencing Commission
[3]Twitter – @OpLastResort
[4]Daily Dot – Alleged Anonymous “Warhead” actually a dud
[5]Verge – Anonymous hacks government site, threatens to expose secrets in response to Aaron Swartz’s death
[6]Daily Dot – Anonymous trolls everyone with encryption keys to warhead
[7]Daily Dot – Anonymous claims it wasn’t behind Operation Last Resort
[8]Pastebin – Anonymous Operation Last Resort v4.9
[9]Pastebin – Operation Last Resort
[10]Pastebin – Warhead Keys
[11]The Pirate Bay – Warhead-US-DOJ-LEA-2013.AES256
[12]Change.org – Anonymous Operation Last Resort: Cease Operations In The Name Of Anonymous Ideals